Managed EDR vs Antivirus: A Primer
Managing your own IT solutions while growing a business is a big task. Add keeping up with evolving cyber security threats and any business owner will feel daunted.
That’s why CYDEF is dedicated to providing tips and tricks to support your business operating safely on the internet.
Today, we’re here to tell you something very important. Your standard anti-virus (AV) solution isn’t up to the task of catching all the threats floating around the internet.
The Threats
One of the biggest threats to your organization’s cybersecurity is … you.
Antivirus really only works when it’s managed and up-to-date. Threats frequently arise and evolve. Without regularly updating your AV, your organization might be exposed.
That’s because your AV can only defend your business when it knows the threat. If a new threat lands on your network, one that’s unrecognised by antivirus, you may experience a breach.
Sometimes crafty hackers are just a step ahead, creating new attacks and threats under the radar. As they deploy the threat, they have the time to breach networks before any antivirus company knows the threat exists.
What AV Won’t Detect
AV actively detects suspicious activity and protects against malware. However, when not updated frequently, it isn’t as effective against advanced threats like zero-day attacks, ransomware and fileless malware.
- Zero-day attacks: These attacks rely on a weakness in an AV product that the manufacturer is unaware of. When the weakness is found, the threat sneaks through.
- Ransomware: These attacks rely on user error. From phishing attacks to email attachments to emails with deceptive links, ransomware depends on individuals to believe an email comes from a valid sender. Once activated, the malware denies access to a system.
- Fileless malware: These attacks rely on an existing software tool. The attack leverages processes in software applications to install malware on an unsuspecting network.
AV solutions catch the known threats. New types of attacks go undetected, sometimes taking up residence on a network for months. That’s why another type of protection is required: on that focuses on detection.
Why your SMB Needs Endpoint Detection and Response
Endpoint Detection and Response (EDR) promises to protect your small and medium-sized enterprise with a different intent. Instead of catching threats at an entry point (like email), EDR monitors what’s happening on your computer systems, identifies unknown behaviours and provides alerts to prompt investigation.
EDR tools analyze network activity, including application launches, device usage and network events. By continuously monitoring what’s happening on the network, EDR tools can be used to track down and eliminate advanced threats before they become a problem.
Functionality: AV vs EDR
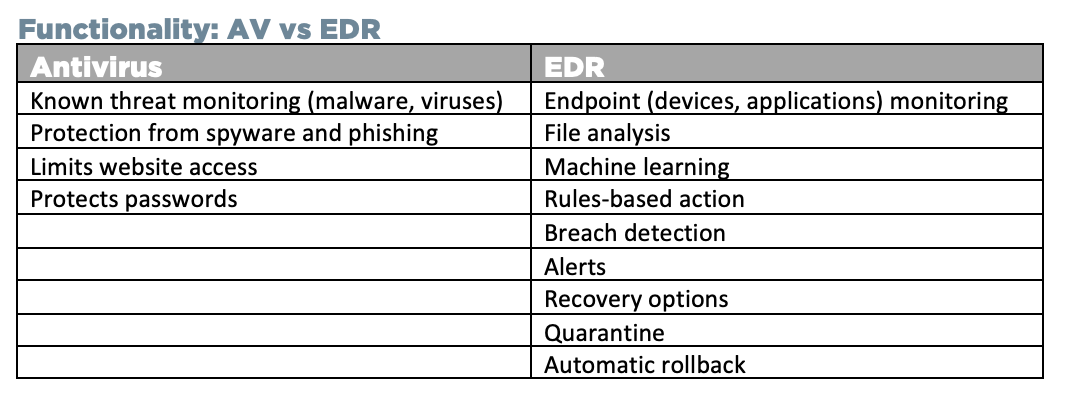
AV and EDR do different jobs. Using the analogy of a castle:
- AV defends the entry points and gates
- EDR monitors activity inside the castle Both tools have a clear benefit. In an advanced threat environment, a layered approach (combing both tools) is ideal.
Managing AV + EDR
The ongoing threat monitoring provided by and EDR tool can require a skilled team, often not an option for small and medium-sized enterprises. These Security Operations teams rely on expert teams demanding immense salaries, specialized skills and heaps of time.
There is, however, an option for those businesses unable to support a dedicated cyber defense team: managed EDR.
Managed EDR provides the same protection, detection and alerts as a Security Operations Centre at the fraction of the price. Solutions like SMART-Monitor, offered by CYDEF, provide fully managed EDR. The skilled team of analysts use a proprietary machine learning tool to track threats, alert your IT personnel, and recommend action. You receive a virtual security operations team, without the expense.
Curious about CYDEF’s SMART-Monitor service or layered security? Check out our recent blog posts on the topic!

CYDEF
Related posts
Recent posts