The Impact of Potentially Unwanted Programs
by Antoine Lemay | Aug 13th, 2020The Impact of Potentially Unwanted Programs
This series covers the more exotic incidents observed at our client sites and explain how SMART-Monitor helps with catching them. Today, we will look at the security impact of having “potentially unwanted programs” in your environment.
What is a PUP?
Potentially unwanted program (or application), a.k.a. PuP (or PuA), is a designation commonly used by anti-virus (AV) vendors to designate a software that is not malware per-se, but that is present on the computer against the computer’s owner will. Common examples of PuPs are:
- Adware: programs forcibly displaying ads to users and hardened against removal;
- Bundlers: programs that download and install other programs in addition to the program you want on a pay-per-install business model. Most users do not consider PuPs to be security risks, but rather a persistent annoyance. They often tolerate the presence of PuPs as the cost of not paying for the software they use. But is that really the case? We will look at a recent PuP case that happened at one of our client’s location.
A side note about minimum privileges
In general, in a corporate environment, users should have access to the minimum amount of software that they need to do their job efficiently. The reason for that is both cost efficiency (more software to maintain generally equals more IT cost) and risk (more potential for security vulnerabilities). If the business upside of having the item in the environment is nil, even if the risk (or the IT cost) is small, it cannot be justified. As such, all non-business relevant software should be removed from corporate environments. Programs that are labelled as PuPs are just the worst of the bunch.
The incident
The incident in this case is pretty simple, but the impact gets more interesting. The victim works for one of our customers that employs a large number of developers. Furthermore, due to the pandemic, most of them are working from laptops instead of coming to the office. In order to keep the company agile and the developers working, almost everyone has admin rights to their machine. You don’t want to have to wait a few days for a developer to install a new dev tool on the machine or for a remote employee to call I.T. just so they can hook up with their home printer. However, that also gives the user to power to install whatever they find on the Internet.
One of the users decided to install Camstudio. However, the download site they use had bundled Camstudio with additional software using the well known “Fusion Core” bundler PuP. This PuP is widely used (here is an example from the official Filezilla installer and often used to bundle inoffensive applications like McAfee web companion. However, in this case, it was used to bundle malicious software.
Using our SMART-Sentinel technology, we were able to trace the execution chain of the initial item and see what other programs were bundled with the software.
The full content is summarized in the following diagram:
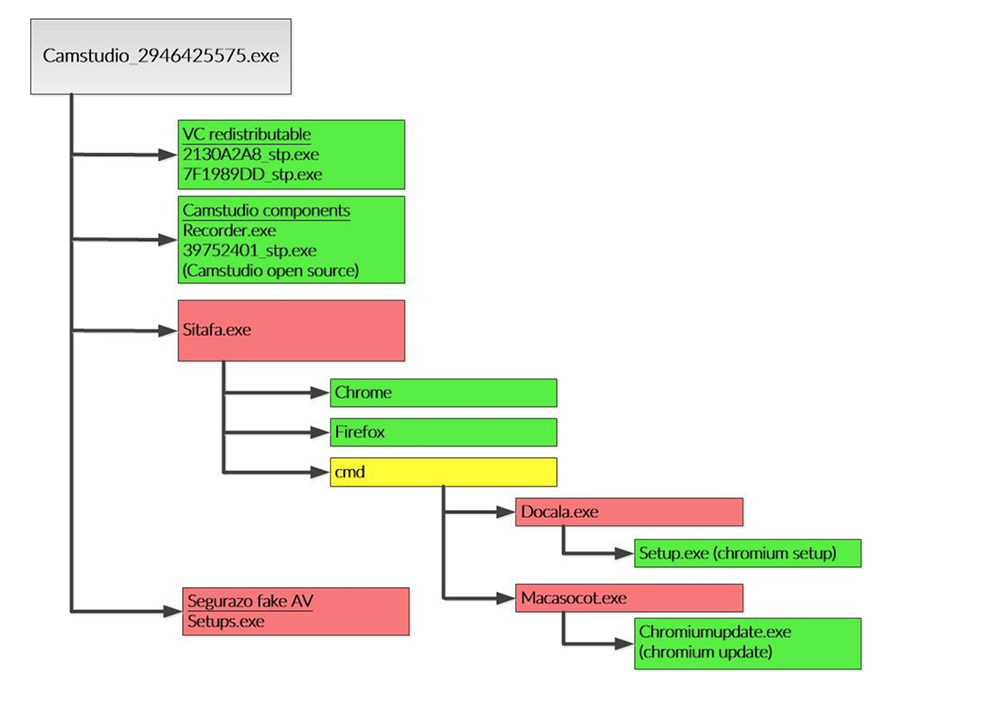
The user started with camstudio_2946425575.exe, a item labelled as a fusion core bundler. That program came with correct Camstudio components (recorder.exe as well as a package that was the non-bundled open source binary). The program also was bundled with Visual C++ redistributable components. All these components are legitimate and required for the software to run.
In addition to the necessary components, the bundler dropped setups.exe, which proceeded to install the Segurazo fake AV, a predatory software that pretends the computer is infected to scare the user into paying the software maker. Based on the activity, it was clear the user realized this software should not be there as the user proceeded to uninstall the software. Unfortunately, Segurazo’s uninstaller is designed not to work as advertised to keep the fake AV on the computer.
Finally, the bundler dropped sitafa.exe, which is labelled as IronSource adware. That particular program started by launching Chrome and Firefox to visit specific web sites and download additional components in the form of .dat files. However, the program then spawns CMD to perform a number of shady actions. Notably, the program changes the web browser start page and concatenates the .dat file to create and execute two exe files (docala.exe and macasocot.exe). The two exes then proceed to run the chromium setup and update processes, suggesting they are chromium apps.
The Final Cost: Time vs Machine Maintenance
In the end, especially due to the presence of the Segurazo fake AV, the IT department decided it was easier to wipe the machine, costing time for both the user and the IT staff. If the problem had not been caught, the degradation of the victim’s machine would have continued, probably requiring more IT effort to resolve the fake AV, with the adware wasting bandwidth and exposing the user to advertising in the meantime.

Antoine Lemay
Chief Scientific Officer
Combining a PhD in Computer Engineering with experience managing cyber intelligence for Canada's largest organizations, Antoine brings a depth of wisdom and expertise in cyber sercurity to the CYDEF team.
Back to blog
Recent posts